The Cybersecurity and Infrastructure Security Agency (CISA) censored Americans critical of mail-in ballots prior to the 2020 election despite knowing that they were at-risk of fraud.
CISA documents obtained by America First Legal show that the Department of Homeland Security agency knew full well there were legitimate criticisms of mail-in ballots but it unconstitutionally advocated for the censorship of Americans questioning them anyway.
The legal watchdog points out that CISA’s acknowledged mail-in ballot issues are as follows:
- CISA knew mail-in and absentee voting are less secure than in-person (i.e., verified voting) voting, confirming warnings by former President Trump and others of increased fraud, and shared these concerns with mainstream media outlets during an unclassified “media tour” the Friday before the 2020 election. However, the mainstream media, having derided the notion that “vote by mail” was less secure than in-person voting, covered up the truth.
- CISA knew that there was no credible evidence to support the claim that in-person voting would spread COVID-19. Yet, it covered up the truth and supported mass vote-by-mail schemes.
- CISA relied upon Deloitte, an accounting and consulting firm, to gather disinformation “narratives” regarding vote-by-mail across social media for the purpose of monitoring and censorship.
CISA knew of mail-in ballot risks, as shown by its own documents.

In a “test run” in September 2020, CISA sought to draw inferences from evidence that in-person voting did not increase the spread of COVID-19.
“Links to a newer study that could not conclude that voting in April primary increased the spread of Covid, refuting an earlier study,” the document said.
CISA was also aware that mass “vote-by-mail” operations posed “major challenges,” including “the process of mailing and returning ballots,” which led to “high numbers of improperly completed ballots (figures not yet released),” and “the shortage of personnel to process ballots in a prompt manner.”
Strikingly, CISA created a chart specifying six examples of “mail-in voting risk”:
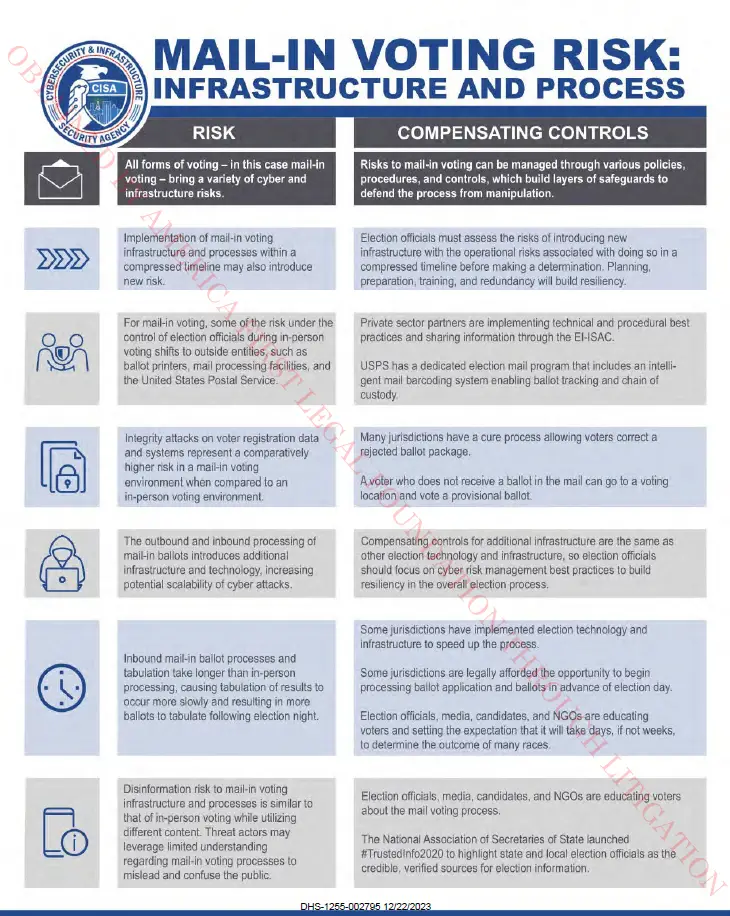
This is summarized by the AFL below (emphasis added):
- “Implementation of mail-in voting infrastructure and processes within a compressed timeline may also introduce new risk.”
- “For mail-in voting, some of the risk under the control of election officials during in-person voting shifts to outside entities, such as ballot printers, mail processing facilities, and the United States Postal Service.”
- “Integrity attacks on voter registration data and systems represent a comparatively higher risk in a mail-in voting environment when compared to an in-person voting environment.”
- “The outbound and inbound processing of mail-in ballots introduces additional infrastructure and technology, increasing potential scalability of cyber attacks.”
- “Inbound mail-in ballot processes and tabulation take longer than in-person processing, causing tabulation of results to occur more slowly and resulting in more ballots to tabulate following election night.”
- “Disinformation risk to mail-in voting infrastructure and processes is similar to that of in-person voting while utilizing different content. Threat actors may leverage limited understanding regarding mail-in voting processes to mislead and confuse the public.”
CISA also noted that “Mail-in Voting 2020 Policy Changes” were being implemented across the United States. Several of these election rule changes were unconstitutional, because they were not implemented through the state legislatures.
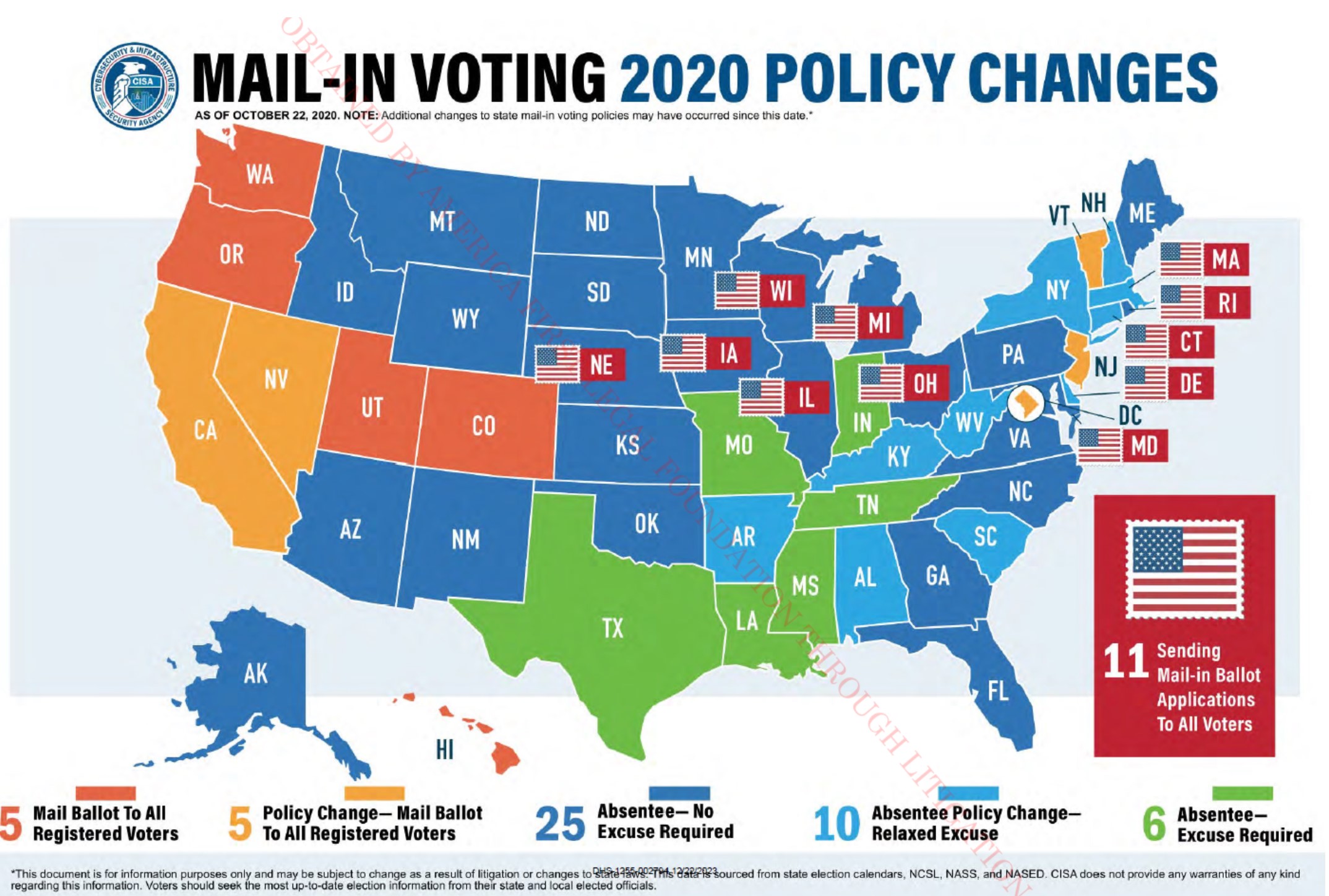
Critically, CISA shared these findings in an “unclassified media tour” on the Friday before Election Tuesday.
Nonetheless, the Washington Post and other such left-leaning outlets ignored the mail-in ballot risks detailed by CISA, and claimed without evidence that CISA Director Chris Kreb was making apolitical “statements about the security of mail-in ballots” that “directly contradict” those asserted by Donald Trump.
CISA appeared to place the greatest emphasis on monitoring and regulating the “narrative” of mail-in voting. CISA appears to have engaged Deloitte to report on “Daily Social Media Trends” in the United States. Election — including narratives about “Vote-By-Mail” — as well as flagging specific social media posts for CISA’s notice.
Among Deloitte’s “flags” to CISA:
- Twitter flagged President Trump’s post that there are “big problems and discrepancies with Mail-in Ballots.”
- “A conservative online activist claimed that Twitter is censoring his tweets about voter fraud to help the Democratic presidential nominee.”
- President Trump “retweeted a political pundit who accused a Democratic Congressional candidate of ‘election fraud’ after thousands of ballots were mistakenly sent to his district.”
- “The Governor of Texas quoted an article from a local news outlet on the state’s recent history of voter fraud convictions and claimed that it reveals “Mail ballot vote fraud in Texas.”
- “A conservative pundit accused Twitter of ‘SUPPRESSING’ a story about the Democratic presidential nominee’s son to help the nominee win the election.”
- “A conservative online activist accused Twitter of censoring her posts about voter fraud she is ‘witnessing here in Nevada,’ and expressed her frustration with Twitter’s disclaimers stating that mail-in ballots are secure.”
As AFL noted, “Deloitte’s reports provided CISA with confirmation that its social media monitoring and censorship apparatus was working. In Missouri v. Biden, the United States Court of Appeals for the Fifth Circuit found that ‘the platforms’ censorship decisions were made under policies that CISA has pressured them into adopting and based on CISA’s determination of the veracity of the flagged information’.”
The House Judiciary Committee and its Select Subcommittee on the Weaponization of the Federal Government discovered that CISA established the Election Integrity Partnership (EIP) to unconstitutionally restrict Americans’ speech.
Director Krebs said before Congress that “narratives are narratives,” hence CISA made no distinction between domestic and international social media activities.

According to congressional investigators, CISA censored whole “narratives”.

As America First Legal summarized:
- CISA knew that in-person voting did not increase the spread of COVID.
- CISA knew mail-in voting was less secure.
- CISA nevertheless supported policy changes to encourage unprecedented widespread mail-in voting.
- CISA formed the EIP to censor narratives relating to mail-in voting.
- CISA broadly monitored social media to detect unapproved “narratives” relating to mail-in voting and to confirm that platforms were adequately censoring them.
Cybersecurity expert Mike Benz recently disclosed in an extensive interview with Tucker Carlson the various ways that CISA and other government-funded agencies pre-censored the public debate around the 2020 election.
“So DHS was basically deputized. It was empowered through this obscure little cybersecurity agency to have the combined powers that the CIA has abroad with the jurisdiction of the FBI at home. And the way they did this, how did… an obscure little cybersecurity agency get this power… was they did a funny little series of switcheroos.”
“So this little thing called CISA — they didn’t call it the Disinformation Governance Board, they didn’t call it the Censorship Agency — they gave it an obscure little name that no one would notice called the Cybersecurity and Infrastructure Security Agency, who its founder said, ‘we care about security so much, it’s in our name twice.’ Everybody sort of closed their eyes and pretended that’s what it was.”
“But it was created by Act of Congress in 2018 because of the perceived threat that Russia had hacked the 2016 election, had physically hacked it. And so we needed the cybersecurity power to be able to deal with that. And essentially on the heels of a CIA memo on January 6th, 2017 and a same day DHS executive order on January 6th, 2017, arguing that Russia had interfered in the 2016 election and a DHS mandate saying that elections are now critical infrastructure. You had this new power within DHS to say that cybersecurity attacks on elections are now our purview.”
“And then they did two cute things. One, they said, mis-, dis-, and and mal- information online are a form of cybersecurity attack. They are a cyber attack because they are happening online. And they said, ‘well, actually Russian disinformation is we’re actually protecting democracy and elections’. We don’t need a Russian predicate after Russiagate died.”
“So just like that, you had this cybersecurity agency be able to legally make the argument that your tweets about mail-in ballots, if you undermine public faith and confidence in them as a legitimate form of voting, was now you were now conducting a ‘cyber attack’ on US critical infrastructure by articulating ‘misinformation’ on Twitter…”
“Yes, you could literally be on your toilet seat at 9:30 on a Thursday night and tweet, ‘I think that mail-in ballots are illegitimate.’ And you were essentially then caught up in the crosshairs of the Department of Homeland Security classifying you as conducting a cyber attack on US critical infrastructure because you were doing ‘misinformation’ online in the cyber realm.”
The most insidious fact of CISA’s censorship operation is that while it was working to censor Americans’ criticism of mail-in ballots, its leadership knew full well that much of this alleged “disinformation” was actually legitimate criticism.
Even more disturbing, despite CISA’s awareness of mail-in ballot risks, and the Covid emergency having come and gone, many states have made no-excuse mail-in ballots a permanent feature of their state elections.
The states are thus knowingly running their elections in a manner that is directly contrary to best election integrity practices. One-day elections, photographic voter IDs, and paper ballots remain the most secure way to run elections in the United States and around the world.
NOW READ:








